Developing strategies for business growth is a cornerstone of the modern organisation. Developing strategies to help avoid business loss is just as important, which means business continuity plans are critical. These documents provide detailed plans on how to keep essential operations running during an emergency in order to minimise losses. Some organisations call these documents “disaster recovery plans.” Others use …
10 Reasons why your business needs a website
There are a lot of good reasons why your company needs a website, below are 10 reasons why its essential to be online now: 1. Convenience for customers Using the Internet to search for businesses and products is much easier and faster than any time in the past. Millions of searches are done everyday and it is commonplace for businesses …
9 Useful Keyboard Shortcuts That Work in Microsoft Word, Excel, and PowerPoint
If you use Microsoft Word, Excel, or PowerPoint, you probably know the keyboard shortcuts to select all (Ctrl+A), copy (Ctrl+C), and paste (Ctrl+V). Did you know there are other helpful keyboard shortcuts that you can use in all three applications? Being able to use the same keyboard shortcuts can make them easier to remember. Here are nine keyboard shortcuts that …
6 Microsoft Office 2016 Details to Look Forward To
Microsoft Office 2016, the latest Windows-based version of the major technology company’s application suite, is scheduled for a release later this year. However, we already know quite a bit about the product, thanks to a preview and testing program that Microsoft has been running. Here are 6 details to look forward to, ahead of the product’s mainstream release: 1. Better …
6 IT Policies To Help Protect Your Company
Many companies rely on IT to help run their businesses. For this reason, they often depend on a set of IT policies to ensure the productive, appropriate, and legal use of IT resources. IT policies establish expectations and regulations for behavior related to company computers and networks. In addition, IT policies detail consequences for employees or customers in the event …
Why 3CX as a Virtual PBX Over Other Hosted Solutions?
Since technology started making its way towards the cloud, a whole array of virtual products have graced the business software and solutions market. When it comes to choosing a virtual PBX for your business, and with so many vendors claiming to offer the perfect solution, it can be a daunting task just narrowing down a shortlist of possible contenders. After …
5 tips on How to Spot a Malicious Email
5 tips on How to Spot a Malicious Email Email spam filtering is much better than it used to be. For example with the anti-spam service I use I get maybe one spam email a week. But no system is perfect and every now and then a malicious email will manage to slip into your inbox, so it’s critically important …
6 Reasons to Use Remote Monitoring to Keep an Eye on Your Systems
6 Reasons to Use Remote Monitoring to Keep an Eye on Your Systems Many IT service providers use remote monitoring tools to gather information and send reports about their clients’ computer systems. Almost anything can be monitored, from routers and firewalls to virus detection and email services. Here are five benefits of using remote monitoring to keep an eye on …
The Top Ten Tips to Protect Yourself from Malware
1. Do not open suspicious looking emails or click on URLs / hyperlinks in such mails. This cannot be stressed enough and is still a major reason for infection. If in doubt, delete! For businesses it is worth employing third party cloud-based email hygiene subscription services (such as our email software). These scan emails before they are delivered. They also offer features such as …
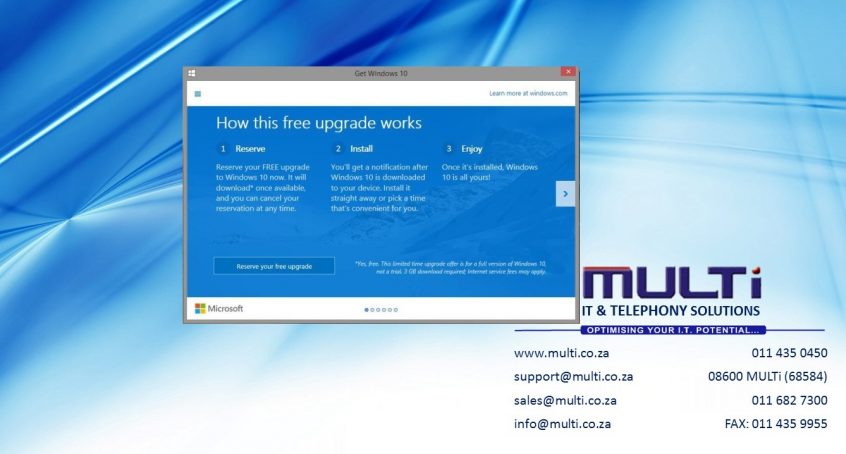
Why you should wait on the Windows 10 Upgrade
Microsoft announced that Windows 10, their latest operating system to grace the computers of this planet, will be launching and made available worldwide on 29 July 2015. As someone who uses the Technical Preview builds every day, they’re almost ready for gold status, but they’re a ways away from it, with a few remaining niggling issues to solve and some …
Protect your Personal Information
You hear about people’s hard earned money being defrauded every day and you may be scared that the same might happen to you. There are better ways to keep safe than to keep all your money hidden under your mattress. The best way to protect yourself is to protect all your personal information and keep it away from thugs. What …
Top 10 Technology Trends for 2015
The 2015 Technology Trends are very exciting as technology is advancing at a faster rate giving us even more features, security and mobility. The latest trends are focused at improving your lifestyle through various ways and means, here are the top 10 Technology Trends for 2015. 1. Computing Everywhere As smart-phone technology advances, smart-phones will be used in new contexts …