IT Managed Services have become more and more popular among small to medium-sized businesses. There are many reasons for the growing move towards Managed Services and below are just a few immediate benefits. 1. Control IT Costs Outsourcing gives you a fixed cost and allows you budget effectively. You are able to use as much of that contract as you need …
What You Need to Know About Creating an IT Budget for 2015
After a long period of recession, spending on business technology is now on the rise. Signs of economic recovery and a more stable operating climate have caused companies to shed their cautious approaches and spend more on IT in 2015. With Electricity supply expected to stabilize and the ever-increasing advancements and benefits of IT for companies the expected IT spend …
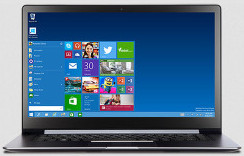
Windows 10 Review and Features
Multi Will be offering the Windows 10 Upgrade pack for FREE On the 21st of January 2015 late Wednesday Night in South Africa the Multi staff were glued to the Windows 10 launch live stream. After all the features and demos we all agreed that Windows 10 is a definite upgrade for everyone using a device. It wasn’t another release of something new …
5 Big Security Threats you could face in 2015
2014 was completely disastrous from a security point of view for companies and people alike. Apple’s iCloud breach saw private celebrity photos leaked, the most memorable security breach of 2014 was Sony Pictures who was thanks to a breach in Apple’s iCloud, Sony Pictures was the victim of it all but crippled the company and the public at large found itself …
Information Security Password strength is key
In today’s technologically driven business marketplace one of most often overlooked points of vulnerability to your business and personal information security is the strength or weakness of the passwords that you define for usage when logging into: your computer network, email provider, online banking, accounting or payroll applications. To underestimate the importance of strong passwords is to leave the door …
It’s time to say goodbye to Windows Server 2003
Technology is advancing at an incredible rate. Consider just how much has changed in the past 12 years, no one uses maps to get around anymore. But back when Window’s Server 2003 (WS 2003) was first released that’s how we did it. Considering what we know now and looking back, a lot of our technology, workloads and processes were inefficient. …
10 Tips for Disaster Recovery Planning
Last week South Africa experienced its worst load shedding since 2008 with R200m worth of lost revenue and damages to the country and businesses. Fortunately no one was killed or badly injured but more than 800 000 businesses were without power and most parts of the country looked more like a dead ghost town than a commercial area. With Generators catching fire and IT hardware becoming corrupt, a disaster recovery plan …
Why your company needs an Internet Policy
With computers and Internet access such an integral part of every business, and the Internet filled with everything from gambling to X-Rated websites, it is critical that every business has an Internet Use Policy in place. This policy can help prevent your employees from accidentally or intentionally causing harm to your company or your company’s reputation. While you don’t want …
3 Ways to Protect Your Data During a Power Outage
[one_half padding=”0 5px 0 0″] The only thing longer than the Load Shedding schedule is the list of damaged equipment and data loss we have seen from it. When Rolling Blackouts and Load Shedding occur, protecting your computer and network may not be on your list of priorities. However, Load Shedding damaged equipment is more common than you think. With the …
The 3 important offerings of Office 365
Trust is the foundation of every good relationship. That’s as true in business as it is in friendship. Today, more than 1.2 billion people worldwide trust Microsoft Office to provide a reliable productivity solution with commercial-grade privacy, security and compliance features to keep their data secured. With more organizations moving to the cloud, and more people using cloud-based services such …
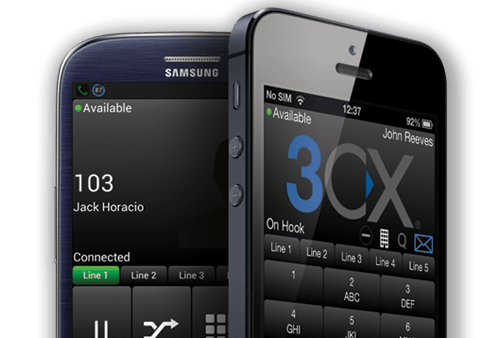
How a Mobile VoIP Client Can Benefit Businesses of All Sizes
Small, medium and large businesses may not have much in common, but one thread that currently runs through companies of all sizes is an increase in mobile working. Whether you own a start-up and are frequently meeting with venture capitalists to seek funding, or you travel the world to make sales for a large corporation, staying in touch with clients …
4 Must Have features for a Business Phone System
If you’ve been researching new phone systems for your business recently, it’s perfectly understandable that your head is spinning. With so many vendors in the marketplace promoting the features of their wares, and the glut of statistics available on the Internet hyping the benefits of various solutions, pinpointing exactly which capabilities your company should employ to meet its communications needs …